Simple and Easy to Start Targeted Attack Email Training Service.
Simple and Easy to Start Targeted Attack Email Training Service.
Features
-
Point 1
- Ideal for first-time training services!
-
Point 2
- Unlimited access to our cloud-based service for just ¥150/month
-
Point 3
- Simple yet feature-rich!
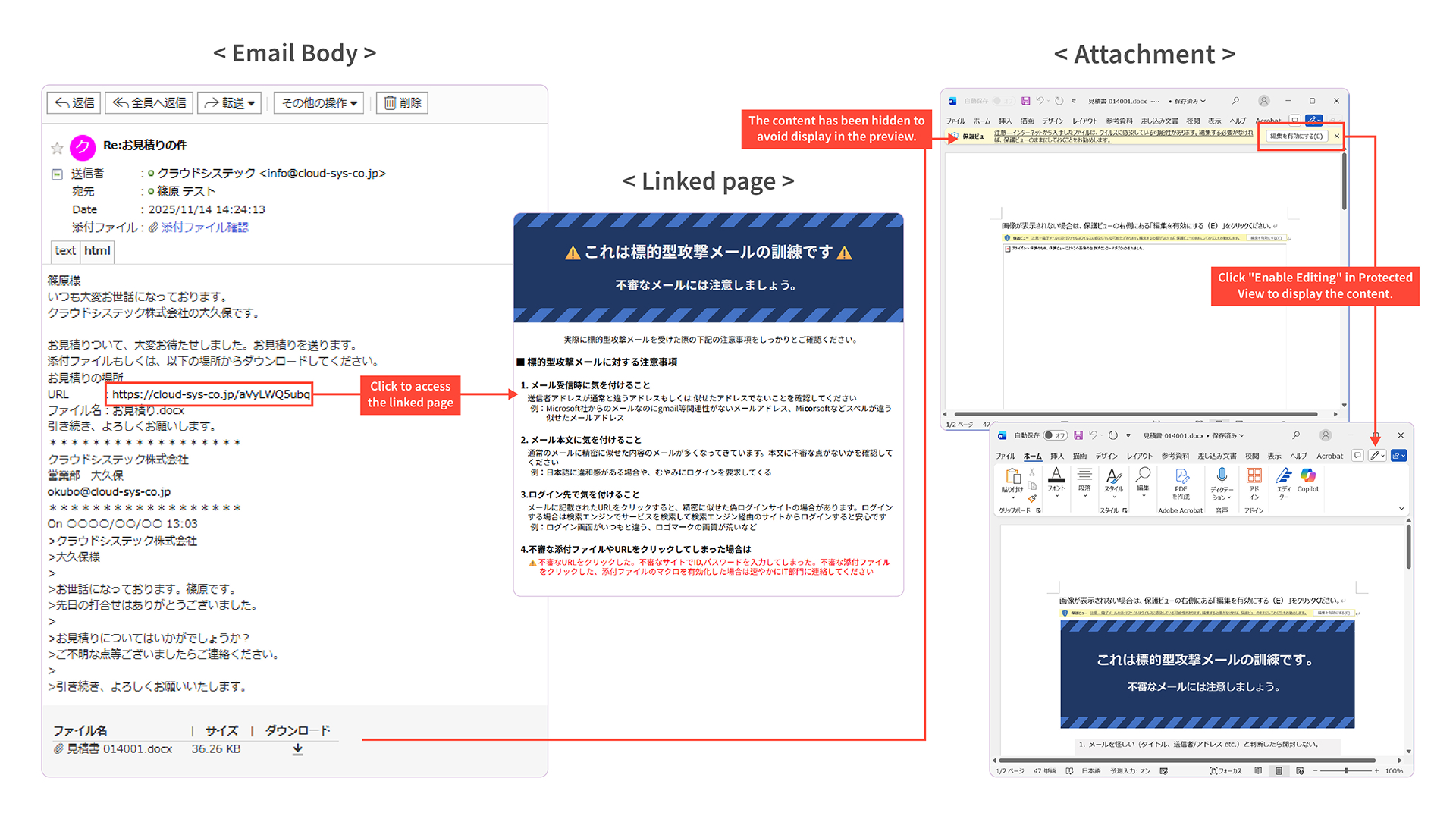
Targeted email attacks differ from mass spam emails in that they are cyberattacks aimed at specific companies or organizations.
They narrow down targets to the individual level, impersonating real emails from past communications and using real names,
making it difficult for ordinary users to detect due to their sophistication.
Countermeasures by systems alone are insufficient, and the targets are no longer just large corporations or government agencies.
All users need training to 'not open suspicious emails.'"